Simple Check for SSL Cert Expiration Monitoring
Monitoring SSL Certificate expiry days can be done in LogicMonitor by making use of datasource SSLCerts- (SSL Certificate Expiration). On the side note, SSL Certificate is used for certifying a web server that does the secured socket layer data encryption between a web server and a client (web browser). SSL Certificate is issued by several organizations/companies so called Certificate Authority (CA) for the purpose of providing the legitimacy of the web servers that encrypt the data for communication. The certificates issued will be digitally-signed by those CA and can be trusted by the client based on Root Certificates installed in the common browsers. It is, however, possible to create a self-signed certificate, which in this case is used for a testing purpose. Data will still be encrypted but the certificate will not be trusted by the client browsers.
When a device with SSL Cert installed has been added to LogicMonitor, rightfully that datasource will be auto-applied, as with other normal datasources, and after some collection cycles, the data of the certificate remaining days to expire should appear. Under the circumstances whereby the monitoring does not work as per normal, common recommendation will be to go through the following simple procedures:
1) Device check, whether or not the SSL Certification has been configured properly
2) Accessibility from collector
3) Data collection test from collector
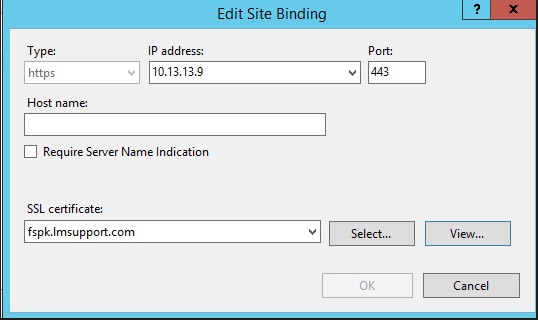
1) For a start is to check if the SSL certificate configuration is properly done in the web server
- Each web server may have a different way of setting up the certificate, the following is an example for NGINX & IIS:
ssl_certificate "/etc/cert/nginx/private/[cert name].crt";
ssl_certificate_key "/etc/cert/nginx/private/[cert name].key";
- An open port check would be good as well with below output from the check (note: port is bound to any interfaces or possibly only one interface on the web server):
Linux:
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN
Windows:
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING
2) The next check will be to access the web server from the collector (obviously the collector must be able to reach to the device where the web server is installed):
Note: Collector debug window is needed for this check, please refer to this article: https://www.logicmonitor.com/support/settings/collectors/using-the-collector-debug-facility/
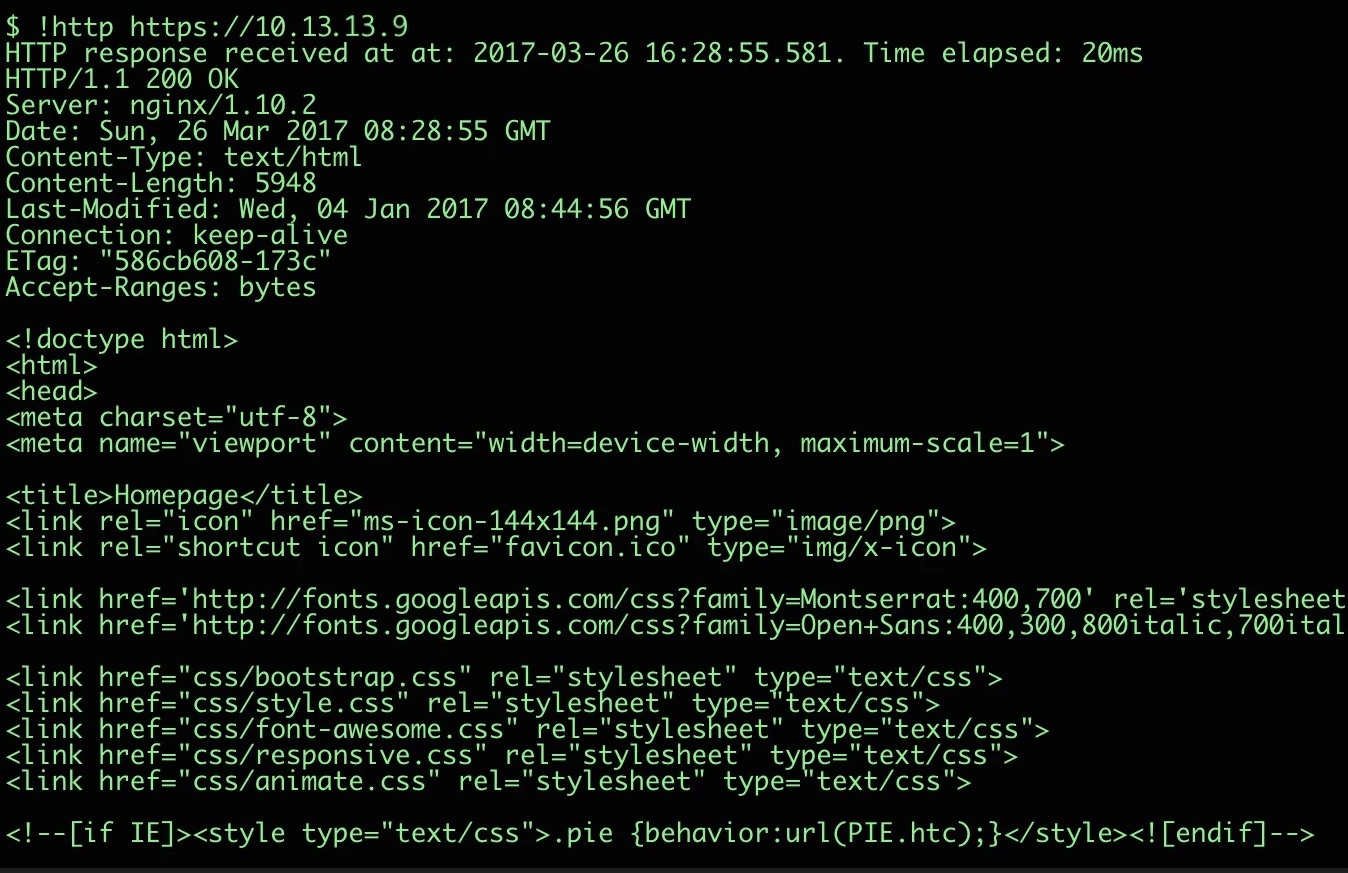
- the main command is simply: !http (help !http will give info for the command itself)
$ !http https://10.13.13.9 HTTP response received at at: 2017-03-26 16:28:55.581. Time elapsed: 20ms HTTP/1.1 200 OK Server: nginx/1.10.2 Date: Sun, 26 Mar 2017 08:28:55 GMT Content-Type: text/html Content-Length: 5948 Last-Modified: Wed, 04 Jan 2017 08:44:56 GMT Connection: keep-alive ETag: "586cb608-173c" Accept-Ranges: bytes
It shows that the web server is accessible at port 443 (HTTPS) with response code 200 as follows:
3) The last one will be to check if data can be collected from the collector which is the remaining days to the expiry of the certificate. Collector debug window is still needed for this check.
For Linux collector:
$ !java -cp ../lib/certexpire.jar CertificateExpire /usr/local/logicmonitor/agent 10.13.13.9 10.13.13.9 443 true Enable debug SSL cert Get the support protocol, protocols=SSLv2Hello,SSLv3,TLSv1,TLSv1.1,TLSv1.2, Get the enabled protocol, protocols=TLSv1,TLSv1.1,TLSv1.2, Try to send request to server. Request send ... TrustManager: checkServerTrusted got 1 certs. Auth type: ECDHE_RSA Exception caught - java.security.cert.CertificateException: Certificate received. Certification 1 [Type: X.509] Issue Date: Mon Jan 02 17:51:51 SGT 2017, Expiration Date: Sat Jul 01 17:51:51 SGT 2017 Got issue date - Mon Jan 02 17:51:51 SGT 2017, expiration date - Sat Jul 01 17:51:51 SGT 2017 97
For Windows collector:
$ !java -cp ../lib/certexpire.jar CertificateExpire "C:\Program Files (x86)\LogicMonitor\Agent" fspk.lmsupport.com fspk.lmsupport.com 443 true Enable debug SSL cert Get the support protocol, protocols=SSLv2Hello,SSLv3,TLSv1,TLSv1.1,TLSv1.2, Get the enabled protocol, protocols=TLSv1,TLSv1.1,TLSv1.2, Try to send request to server. Request send ... TrustManager: checkServerTrusted got 1 certs. Auth type: DHE_RSA Exception caught - java.security.cert.CertificateException: Certificate received. Certification 1 [Type: X.509] Issue Date: Thu Feb 02 03:16:57 PST 2017, Expiration Date: Sat Feb 02 03:16:57 PST 2019 Got issue date - Thu Feb 02 03:16:57 PST 2017, expiration date - Sat Feb 02 03:16:57 PST 2019 660
- The basic command is: !java and complete format would be:
!java -cp ../lib/certexpire.jar CertificateExpire [collector installation folder] [device name/IP address] [device name/IP address] 443 true
Note:
* certexpire.jar is in the library of the collector agent
* device name/IP address is the web server that is registered/added into the LogicMonitor portal
* collector folder is: either "C:\Program Files (x86)\LogicMonitor\Agent" or /usr/local/logicmonitor/agent
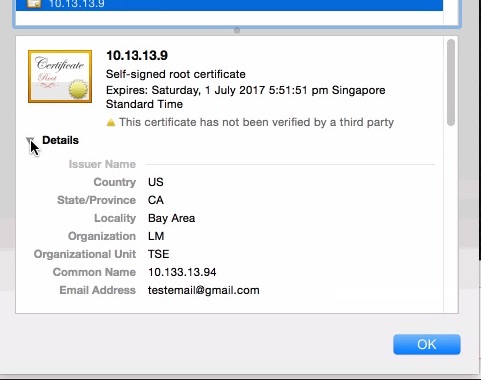
The data collected can be verified on the device where the SSL Certificate is installed by accessing the web server in the browser and view the detail of the certificate loaded in the browser as follows:
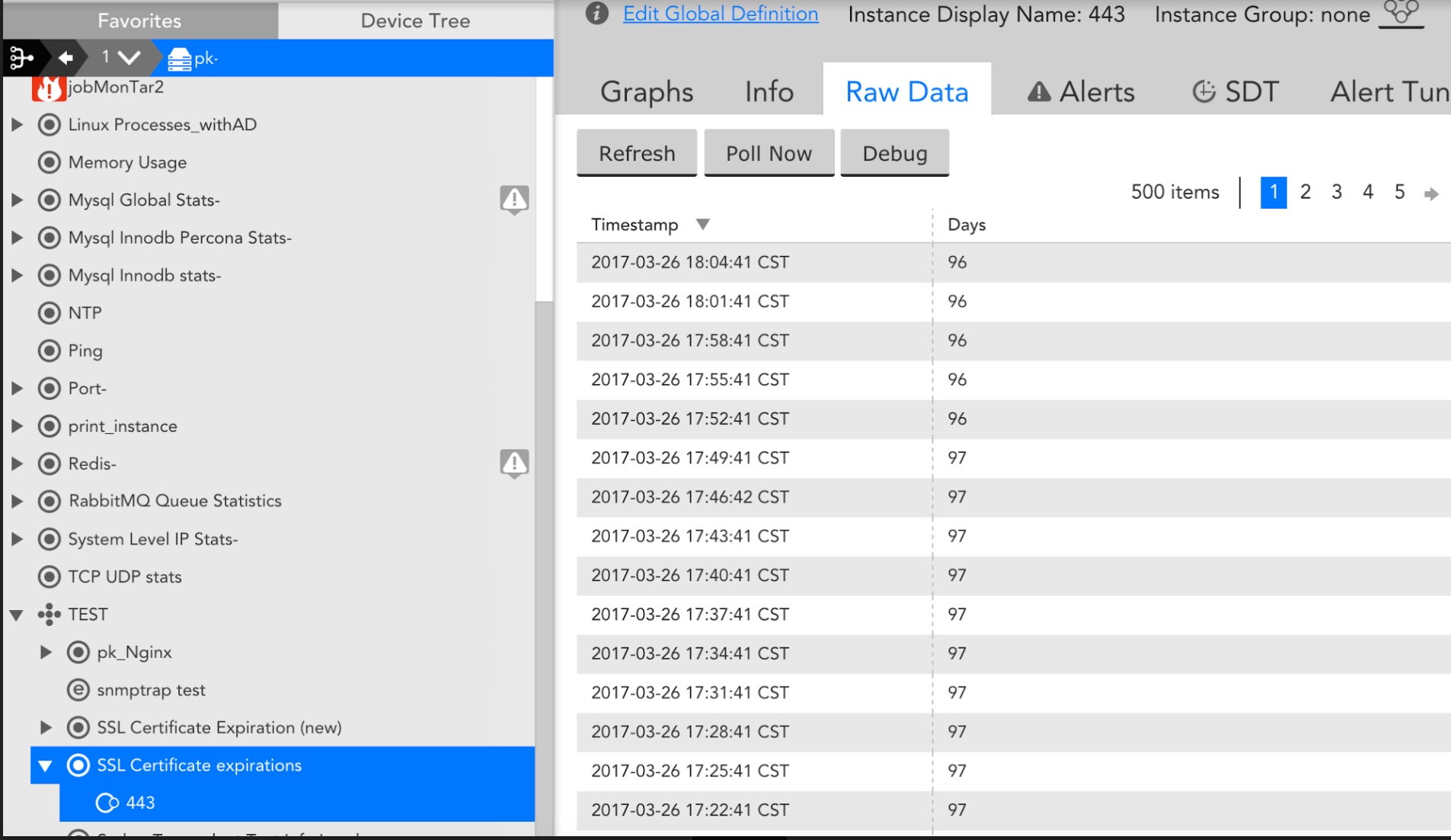
Having gone through all the above-mentioned checks and the results are good, it will produce this monitoring in LogicMonitor as follows: